Hackers Went Looking for a Backdoor in High-Security Safes—and Now Can Open Them in Seconds
Hackers Went Looking for a Backdoor in High-Security Safes—and Now Can Open Them in Seconds
In a shocking revelation, a group of hackers have successfully found a backdoor in…

Hackers Went Looking for a Backdoor in High-Security Safes—and Now Can Open Them in Seconds
In a shocking revelation, a group of hackers have successfully found a backdoor in high-security safes, allowing them to open them in mere seconds.
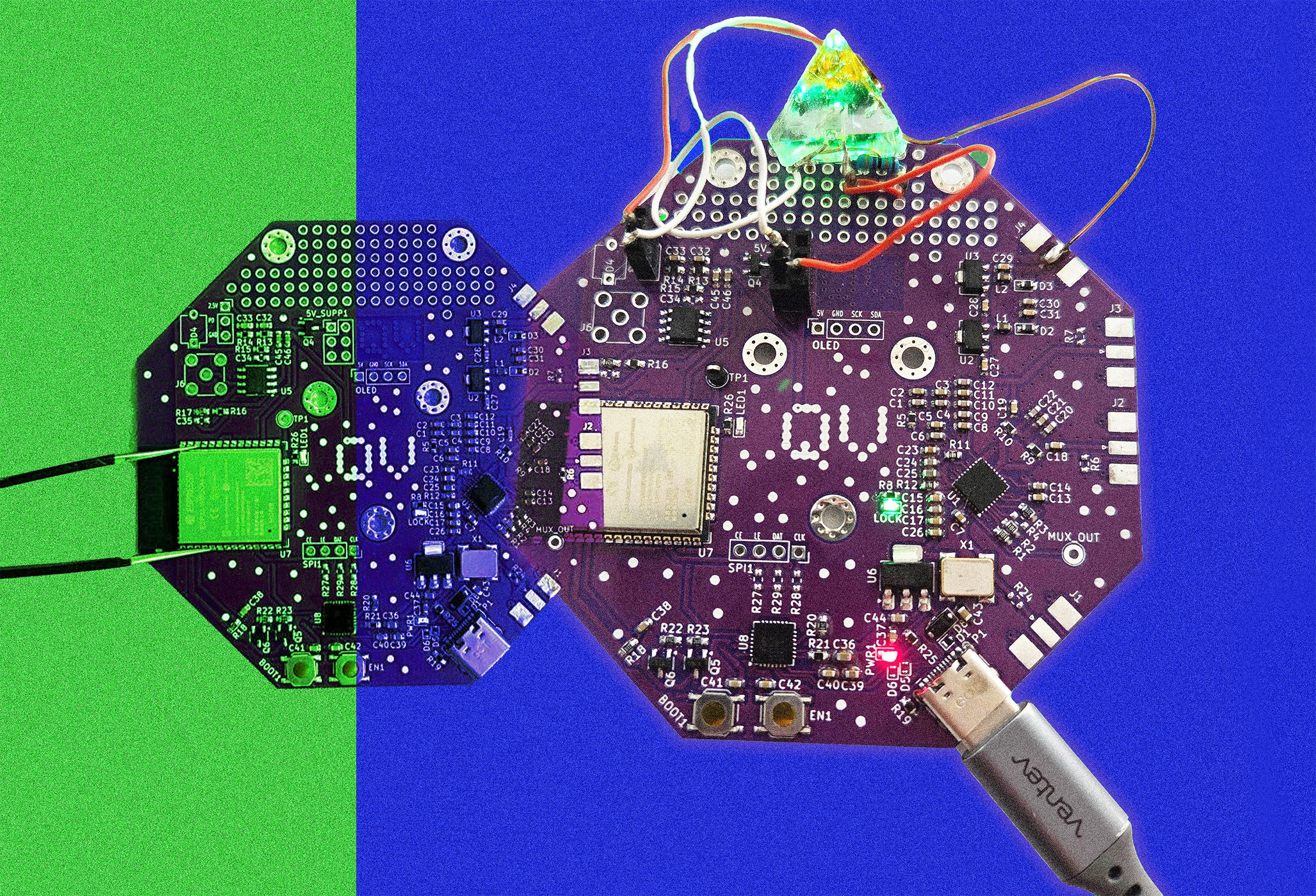
The group of hackers, known for their expertise in bypassing security systems, managed to exploit a vulnerability in the safes’ electronic locking mechanisms.
With this newfound knowledge, these hackers can now gain access to these safes with ease, potentially putting valuable assets at risk.
Security experts are alarmed by this discovery and are warning businesses and individuals to strengthen their security measures to prevent falling victim to such attacks.
The implications of this security breach are far-reaching, as it calls into question the reliability of high-security safes that were once believed to be impenetrable.
Companies that store sensitive information and assets in these safes are now scrambling to find alternative security solutions to protect their valuables.
Law enforcement agencies are also investigating the matter, aiming to track down the hackers responsible for this unprecedented breach.
This incident serves as a stark reminder of the constant threat posed by cybercriminals who are constantly evolving their tactics to exploit weaknesses in security systems.
It is imperative for businesses and individuals to stay vigilant and proactive in securing their assets and information to prevent falling prey to such cyber attacks.
As the investigation into this security breach continues, the cybersecurity community is working tirelessly to develop countermeasures to protect against similar future threats.